Why OpenAI Key Rotation Is a Leadership Priority Now
As soon as OpenAI reaches development or production workflows, the API key becomes critical infrastructure. A leaked key burns budget, enables unauthorized usage, and can take integrations down. This post is Part 1 of our guide to the OpenAI API and keys. In Part 2 we will present a Python‑based admin CLI that enables administration via the command line—including automatable key rotation. The companion article can be found here: Part 2: OpenAI Admin CLI: Security, Cost Control, and Automation for Enterprise Admins.
This guide shows how to establish OpenAI key rotation as a reliable process: zero downtime, clear ownership, clean automation, and verifiable controls.
Principles for Handling OpenAI API Keys Securely
The following rules form the foundation of robust key governance:
- One key per person and context: Assign each team member their own, personal API key. Do not share keys. This keeps usage and accountability traceable.
- No client‑side use: API keys do not belong in browsers, mobile apps, or any other client‑side environment. Always route requests through your backend service.
- Never commit to a repository: Even private repos are not a safe place for secrets. Use environment variables or a secret manager.
- Observe rather than trust: Regularly review usage, costs, and patterns in the provider dashboard. Rotate immediately if you detect anomalies or suspect exposure.
Environment variables instead of hardcoding
Use consistent names like OPENAI_API_KEY. This standardizes deployment and helps avoid accidental leaks.
Windows (cmd):
setx OPENAI_API_KEY "<yourkey>"Open a new shell and verify:
echo %OPENAI_API_KEY%macOS/Linux (zsh):
echo "export OPENAI_API_KEY='yourkey'" >> ~/.zshrc
source ~/.zshrc
echo $OPENAI_API_KEYRead the key from the environment in Python/Node:
import os
OPENAI_API_KEY = os.environ["OPENAI_API_KEY"]const OPENAI_API_KEY = process.env.OPENAI_API_KEYInsights into our tech stack and reference projects from our development department are available at admin-code.de.
Use secret management
Use dedicated solutions such as HashiCorp Vault, cloud secrets managers, or your CI/CD platform’s secret functionality. Advantage: permissions, rotation, audit trails, and encryption are centrally managed. We cover how secrets flow cleanly through pipeline processes in this article: GitLab CI/CD for Administrators – a practical guide to automated deployments.
Rotation strategy: scheduled, event‑driven, verifiable
A good strategy combines fixed intervals with event triggers.
- Fixed intervals: Define a reliable cadence (e.g., every 60–90 days). Consistency matters more than the exact number.
- Event triggers: Rotate immediately if you suspect or confirm a leak, see implausible usage, or when people with access leave the company or the project.
- Map access and usage: Track where each key is used (services, deployments, cron jobs, functions) and who/what has access. This is the only way to avoid blind spots and downtime during the switch.
Naming conventions and scope
Clear names speed up operations and forensics. Patterns that work well:
- Production/Staging keys:
YY-MM-Customer-Project-[Prod|Staging](e.g.,25-10-AI-TicketNG-Prod) - Individual keys:
YY-MM-Employee-Project-Device(e.g.,25-10-JB-TicketNG-Apple)
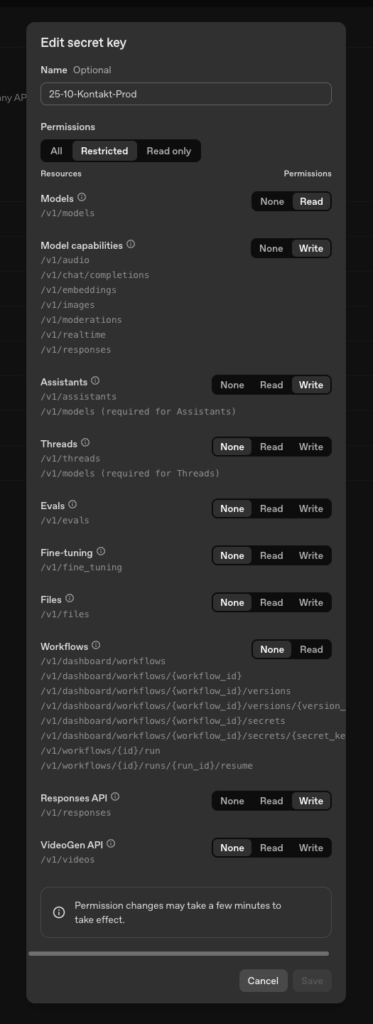
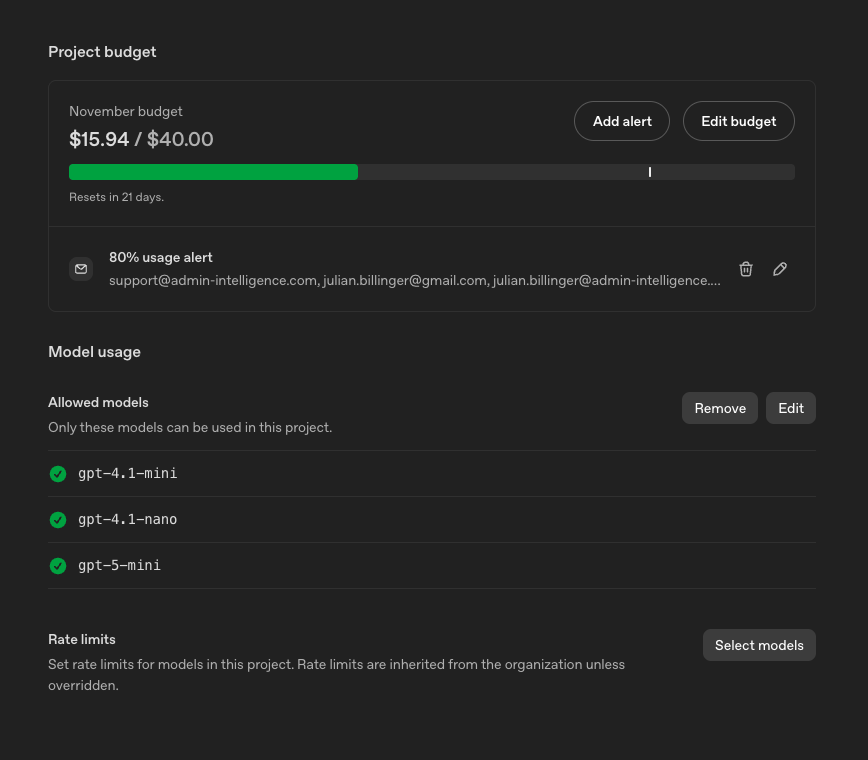
Add minimal permissions (Least Privilege) per key and restrict usage to the exact environments where the key is required. For cost control, a whitelist of “Allowed Models” has proven effective. Only include explicitly approved models to avoid enabling expensive variants by accident.
Zero‑downtime rotation in practice
The goal is a smooth switch with no service interruption:
- Create a new key (Key B): Create the new key and grant it the same permissions/scope as the existing one (Key A).
- Prepare the deploy: Store Key B in your secret store (e.g., as a new secret version label). Keep Key A active in the meantime.
- Rollout: Update applications to use Key B. Start with a canary rollout or staging environment, then roll out in production gradually.
- Validate: Monitor logs, error rates, and costs. Verify that all relevant services use Key B.
- Revoke the old key: Once Key B is live everywhere, disable or delete Key A.
Tip: If your orchestration system supports it, keep two secret versions in parallel during rollout and switch via feature flag/config toggle.
Example: rotation with GitLab CI/CD and Vault (schema)
# .gitlab-ci.yml (excerpt)
stages: [rotate]
rotate-openai-key:
stage: rotate
image: alpine:3.20
rules:
- if: "$ROTATE_OPENAI == 'true'"
script:
- echo "Fetch new key from Vault (path/version)"
- export OPENAI_API_KEY=$(vault kv get -field=value secret/openai/prod)
- echo "Redeploy services with new secret version"
- kubectl rollout restart deploy/my-api
only:
- protectedNo key lives in repositories; CI reads it from the secret store at deploy time and propagates it to the target environment. Further insights into our CI/CD stack, reference projects, and contacts of our development department are available at admin-code.de.
Learn more about secure pipelines in GitLab CI/CD for Administrators – a practical guide to automated deployments and in our services for GitLab CE.
Common leak paths—and how to close them
- Client‑side code (web/app): Never embed keys. Use a backend proxy.
- Git repository: Enable secret scanning/pre‑commit hooks. Rotate immediately if a key is committed, even if the repo is private.
- Logs and crash dumps: Mask Authorization headers, payloads, and environment variables in logs. Check log exporters and APM agents.
- Build artifacts: Ensure images, bundles, and releases contain no keys. Automated scans help.
- Collaboration tools: Never share keys in chat, tickets, or wikis in cleartext. Use one‑time shares via your secret manager.
For detecting abuse and suspicious activity, a SIEM solution is worthwhile. Our overview Wazuh SIEM – Open‑source security made clear shows how to correlate log data centrally and trigger alerts.
Incident playbook: suspected leaked OpenAI key
Act deterministically, not frantically:
- Immediate action: Create a new key, deploy it, disable the old key.
- Determine scope: Where was the old key used? Which systems are affected? Check deployments, cron jobs, functions, test environments.
- Forensics: Analyze logs, costs/usage, the time of the leak, commit history, CI runs, artifacts.
- Preventive hardening: Enable secret scanning, pre‑commit hooks, tighten permissions, review the Allowed Models list, adjust the rotation cadence.
If you actively monitor API usage, you will detect anomalies faster. For next steps in secret governance, see our comparison Vaultwarden vs Passbolt – the comprehensive password manager comparison for admins and teams.
Specifics for OpenAI integrations
- Dashboard management: Organize memberships and API keys centrally in the provider dashboard. Create dedicated keys for Prod/Staging/Test and restrict their use per environment.
- Cost control: Use an “Allowed Models” whitelist per environment/project to avoid accidental use of expensive models. Store this as a policy close to code (e.g., YAML/policy) that is checked in the CI gate.
- Permissions: Separate personal keys (for development/debugging) from technical keys (for deployments). Assign both types clear roles and expirations (organizational: follow‑ups, tickets, calendar reminders).
- Auditing: Document creation, rotation, deactivation, and ownership changes for each key. Without a clean audit trail, forensics is hard.
OpenAI Admin CLI: administration and rotation with Python
For larger organizations, command‑line automation makes sense. Our Python‑based OpenAI Admin CLI manages organizations via the Admin API. It supports user and project management, creating service accounts, and administering API keys including automatable rotation. You can also control rate limits, get detailed usage analytics (completions, embeddings, images, audio), and keep an eye on costs. Output is available as tables or JSON with flexible filtering and grouping options. This helps with audits, cost monitoring, and running production deployments.
More details will follow in the companion article: OpenAI Admin CLI – Admin API management.
Minimal example: clean loading in a container
Docker Compose (shortened):
version: "3.9"
services:
api:
image: ghcr.io/acme/my-openai-service:latest
environment:
OPENAI_API_KEY: ${OPENAI_API_KEY}
secrets:
- source: openai_api_key
target: openai_api_key
secrets:
openai_api_key:
external: true # e.g., from Docker Swarm/K8s/VaultApplication (Node.js):
import express from 'express'
const app = express()
const OPENAI_API_KEY = process.env.OPENAI_API_KEY
if (!OPENAI_API_KEY) throw new Error('OPENAI_API_KEY not set')
// Initialize OpenAI client …Rotation is performed by pointing the secret version alias (e.g., openai/prod:current) in the secret store to the new key. Restarting/reloading the deployment picks up the new version; the old version then becomes invalid. How we implement container deployments in client projects and the technologies we use are shown at admin-code.de.
Checklist for resilient OpenAI key rotation
- One key per person/service, no shared keys
- No keys on the client, no keys in repos
- Unified naming convention, documented scope
- Allowed Models whitelist per environment/project
- Secret manager & established CI/CD automation
- Fixed rotation plan plus event triggers for suspicions/changes
- Zero‑downtime process: B → rollout → validation → revoke A
- Monitoring, SIEM/alerts, cost/usage metrics
- Audit trail for creation, rotation, deactivation
If you use OpenAI in production, an architecture review for security, cost control, and operational excellence is worthwhile. The team at ADMIN INTELLIGENCE supports integration and governance—from policies (“Allowed Models”) to CI‑driven rotation. Reference projects, our tech stack, and the focus areas of our development department are available at admin-code.de. Learn more in our services for AI & LLM and GitLab CE. The next part on our OpenAI Admin CLI with automatable rotation will appear here: OpenAI Admin CLI – Admin API management. If you want help implementing this, get in touch—pragmatic and goal‑oriented support is what we do.

Project Manager, Lead Dev
